
As we stand on the brink of a quantum revolution, understanding quantum key distribution becomes crucial. Quantum keys promise a level of security that traditional encryption methods can’t match. Let’s delve into the various protocols and advancements that make this possible.
Quantum Key Distribution: The Basics
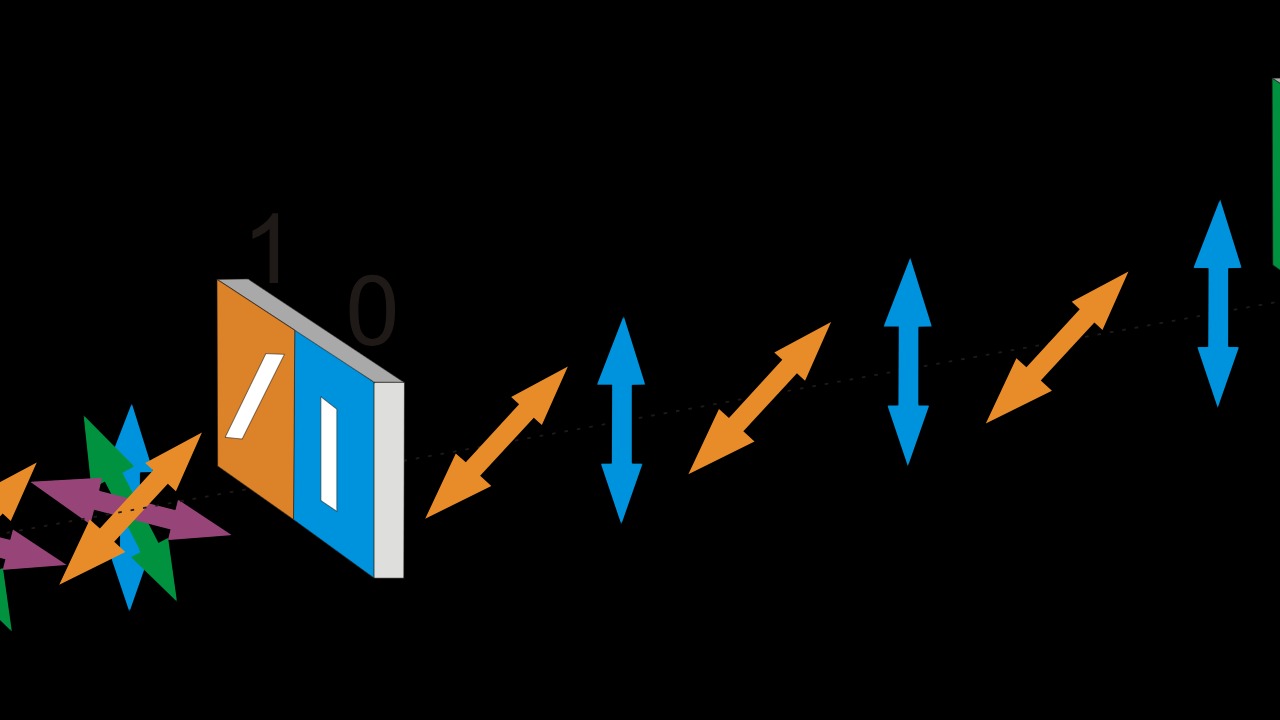
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to secure communication. Unlike classical encryption, which relies on complex mathematical problems, QKD uses quantum bits, or qubits, that can exist in multiple states simultaneously. This inherent unpredictability ensures that any attempt to intercept the key alters its state, alerting both parties to the intrusion.
The beauty of QKD lies in its promise of unconditional security. In a world where quantum computers can potentially break conventional encryption, QKD offers a future-proof solution. Governments and organizations, like the European Union, are investing heavily in this technology to safeguard sensitive information.
BB84 Protocol: A Quantum Leap in Security

The BB84 protocol, introduced in 1984 by Charles Bennett and Gilles Brassard, is the first and one of the most well-known quantum key distribution protocols. It employs polarized photons to transmit cryptographic keys. The protocol’s security is based on the Heisenberg Uncertainty Principle, which ensures that any attempt to measure the photons’ states disturbs them, thus revealing eavesdropping attempts.
Several real-world implementations have demonstrated BB84’s effectiveness. For instance, the Chinese Micius satellite successfully used this protocol to establish a secure link between ground stations thousands of kilometers apart, showcasing its potential for global secure communication.
E91 Protocol: Entanglement at Its Finest

The E91 protocol, developed by Artur Ekert in 1991, takes advantage of quantum entanglement. Unlike BB84, which uses individual photons, E91 employs entangled photon pairs. When one of the entangled particles is measured, its counterpart instantly reflects that change, regardless of the distance separating them.
This protocol is particularly intriguing due to its reliance on the fundamental properties of quantum physics, providing a robust defense against potential threats. Experiments have demonstrated that E91 can achieve high levels of security, making it a cornerstone in the field of quantum cryptography.
Continuous Variable QKD: Beyond Photons
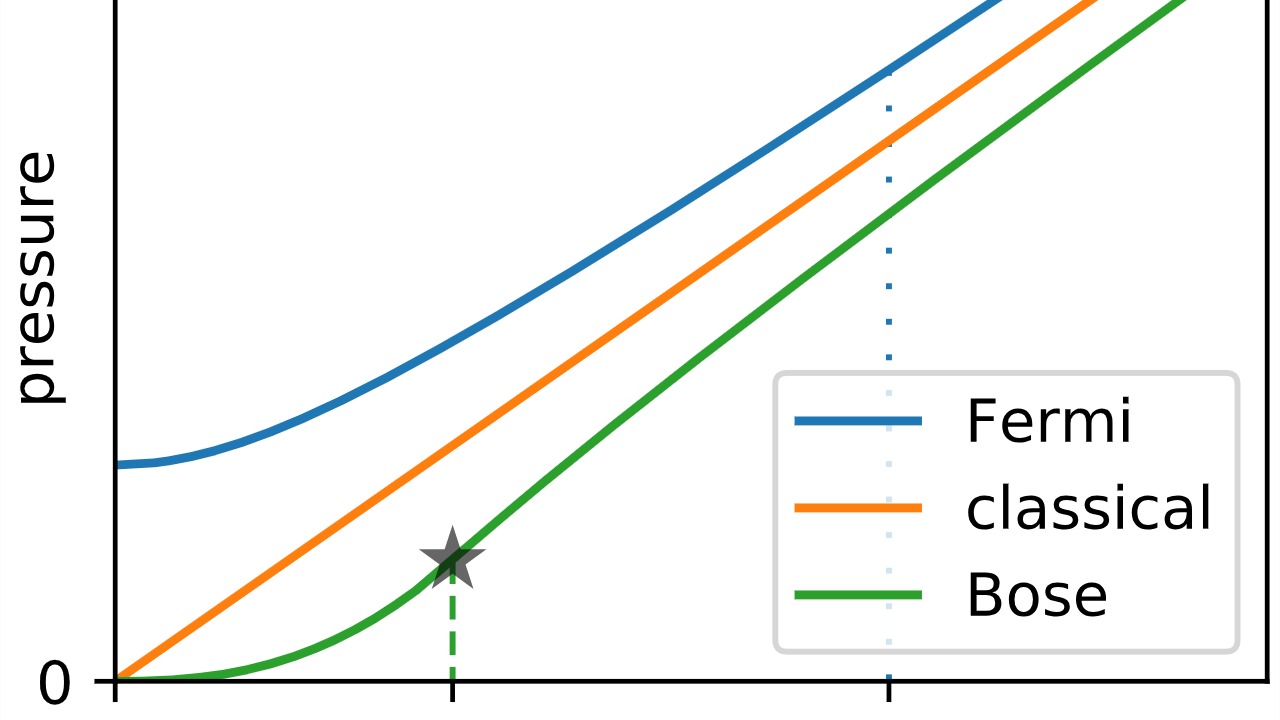
Continuous Variable Quantum Key Distribution (CV-QKD) offers an alternative to discrete-variable protocols like BB84 and E91. Instead of relying on individual photons, CV-QKD uses continuous properties of light, such as amplitude and phase, to encode information. This approach can be integrated with existing telecommunication infrastructure, making it a practical choice for widespread adoption.
CV-QKD systems have shown promising results in terms of range and data rate, positioning them as a viable option for secure communication networks. Their compatibility with current technology makes them an attractive choice for future-proofing our digital communications.
Device-Independent QKD: Trusting the Math

Device-Independent QKD (DI-QKD) aims to eliminate trust in the hardware used to implement quantum key distribution. Instead of relying on the assumption that devices are functioning correctly, DI-QKD leverages the laws of quantum physics to ensure security, regardless of potential flaws in the devices themselves.
This approach is particularly important in scenarios where device integrity cannot be guaranteed. By focusing on the mathematical foundations of quantum mechanics, DI-QKD enhances security, providing an additional layer of assurance against potential vulnerabilities.
Measurement-Device-Independent QKD: Closing the Loopholes
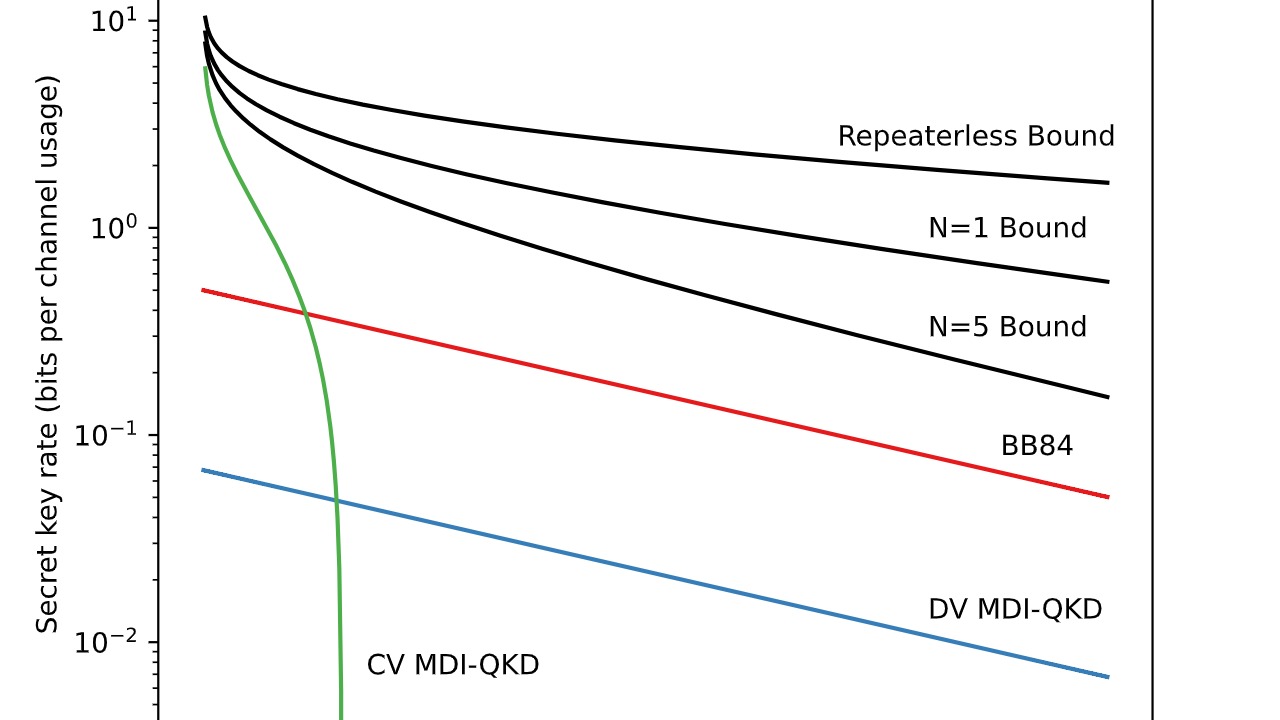
Measurement-Device-Independent QKD (MDI-QKD) addresses vulnerabilities associated with the measurement devices used in QKD systems. By decoupling the measurement process from the security of the key distribution, MDI-QKD closes potential loopholes that could be exploited by attackers.
This protocol has gained attention for its ability to enhance the robustness of quantum communication systems. By mitigating risks associated with measurement devices, MDI-QKD ensures that even if the devices are compromised, the security of the key remains intact.
Twin-Field QKD: Extending the Range
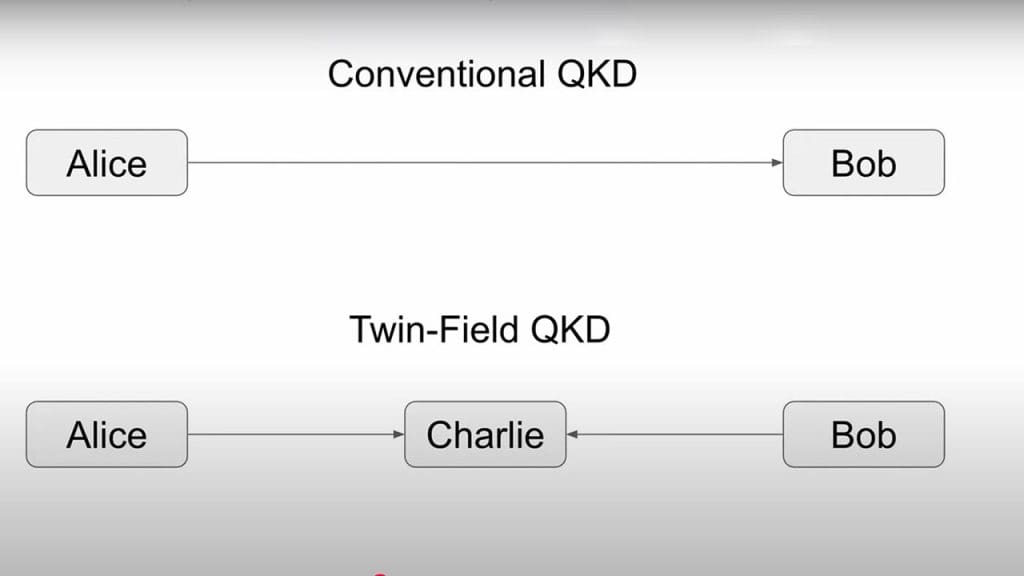
Twin-Field QKD (TF-QKD) is a breakthrough in overcoming distance limitations of traditional QKD systems. By using a shared reference field between two communicating parties, TF-QKD significantly extends the range of secure quantum communication, making it feasible over long distances without the need for trusted repeaters.
This advancement has opened new possibilities for global secure communication networks. The ability to transmit keys over longer distances without compromising security is a game-changer, particularly for applications requiring extensive reach.
Post-Quantum Cryptography: Preparing for the Future

While QKD offers a promising solution for future-proof encryption, post-quantum cryptography focuses on developing classical algorithms resistant to quantum attacks. Researchers are working on new mathematical frameworks that can withstand the power of quantum computing.
As quantum computers become more prevalent, the need for post-quantum cryptography becomes urgent. Organizations are urged to prepare by integrating these new algorithms into their security infrastructure, ensuring data remains secure even in a quantum-powered future.