
Recent technological advancements have made cars smarter and more connected, but they have also introduced unexpected vulnerabilities. One such vulnerability involves hackers exploiting tire pressure monitoring systems (TPMS) to unlock and potentially control vehicles. Understanding how these cyber threats operate and what can be done to mitigate the risks is crucial for both manufacturers and consumers.
The Mechanics of Tire Pressure Monitoring Systems (TPMS)
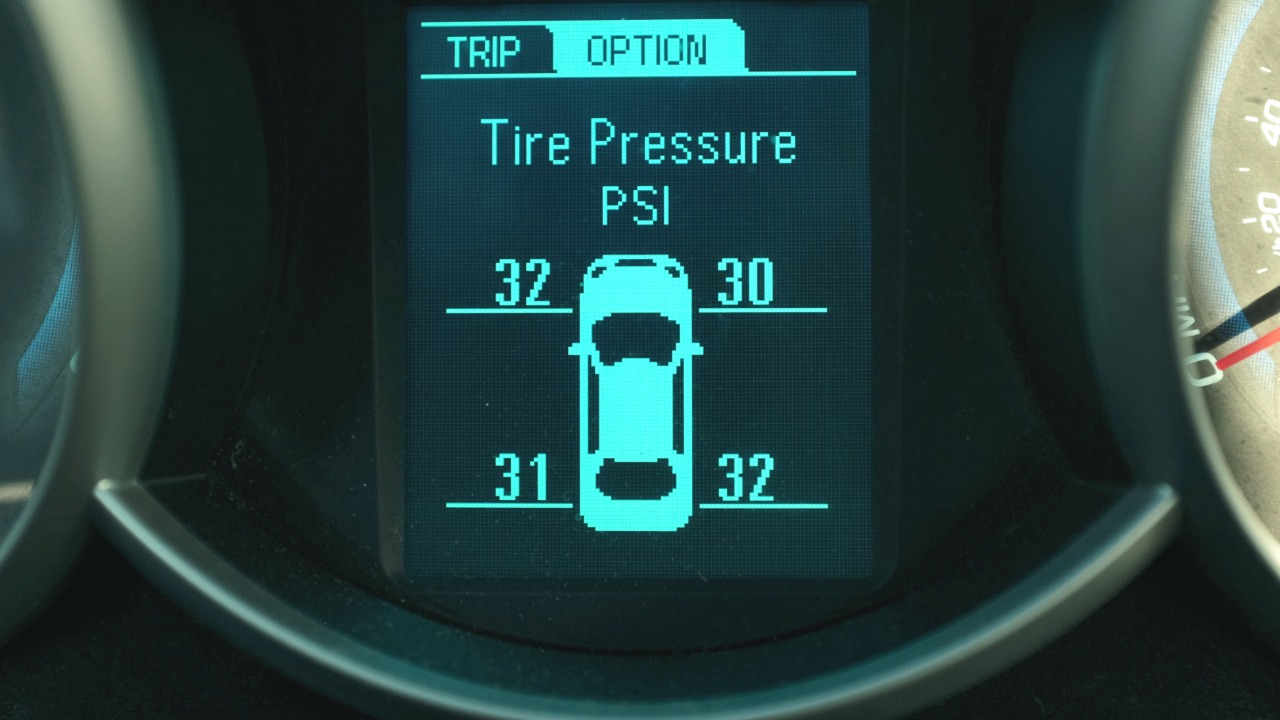
How TPMS Works
Tire Pressure Monitoring Systems (TPMS) have been integrated into vehicles primarily to enhance safety. These systems alert drivers when tire pressure is too low, which can help prevent accidents and improve fuel efficiency. The technology relies on sensors placed inside each tire that communicate wirelessly with the vehicle’s central system, providing real-time data on tire pressure.
The communication between tire sensors and the vehicle involves a wireless signal, which is typically unencrypted. This lack of encryption is where the problem begins. The data transmitted from the tire sensors is usually sent to a radio frequency (RF) receiver in the car, which then processes this information to inform the driver. Unfortunately, this open communication channel is an invitation for hackers to intercept and manipulate the data.
Security Weaknesses
The primary security weakness in TPMS lies in its lack of encryption. Because the data is transmitted wirelessly without adequate protection, it becomes susceptible to interception and manipulation. This vulnerability has been identified in various car models, including some from major manufacturers. For instance, a study conducted on 2010 and 2011 models of vehicles revealed that their TPMS could easily be hacked using simple tools, allowing unauthorized access to the vehicle.
In many cases, the TPMS signals can be intercepted from as far as 40 meters away, making it possible for hackers to exploit these systems without even having to be in close proximity to the vehicle. The implications of such vulnerabilities are significant, as they open the door to more serious cyber threats beyond just unlocking cars.
Exploiting TPMS: The Hacker’s Approach
Techniques Used by Hackers
Hackers have developed various techniques to exploit TPMS vulnerabilities. One common method involves using radio frequency identification (RFID) tools to intercept the unencrypted signals between the tire sensors and the vehicle’s central system. By capturing these signals, hackers can decode the information and use it to unlock the car or even interfere with other vehicle systems.
Some hackers utilize specialized software and hardware tools, such as software-defined radios (SDRs), to manipulate TPMS data. These tools allow them to send false signals to the vehicle, potentially causing the car to misinterpret the tire pressure data and take unintended actions. Some documented incidents have shown how easily these techniques can be deployed, raising concerns about the overall security of vehicle systems.
Real-World Incidents
There have been several real-world incidents where TPMS vulnerabilities were exploited by hackers. In one notable case, researchers demonstrated how they could unlock a car by intercepting and manipulating TPMS signals. This demonstration highlighted the potential for hackers to gain unauthorized access to vehicles, posing a threat to both the security and safety of vehicle owners.
The impact on vehicle owners can be severe, as these vulnerabilities not only compromise the security of their cars but also pose potential safety risks. For instance, hackers could potentially cause a vehicle to display incorrect tire pressure readings, leading to dangerous driving conditions. Such incidents underscore the need for improved security measures to protect against these types of cyber threats.
The Implications for Vehicle Security

Wider Security Concerns
The vulnerabilities found in TPMS are indicative of a broader issue with vehicle cybersecurity. As cars become increasingly connected, the potential attack surface for hackers expands. TPMS is just one of many systems in modern vehicles that are susceptible to cyber attacks, and its exploitation could serve as a gateway for hackers to access other critical vehicle systems.
For example, once hackers gain access through TPMS, they may be able to access other systems such as the vehicle’s infotainment or navigation systems. This could allow them to track the vehicle’s location, eavesdrop on conversations, or even take control of the vehicle. The potential for such wide-reaching security breaches highlights the urgent need for improved cybersecurity measures in the automotive industry.
Industry Response
Automakers are beginning to recognize the importance of addressing cybersecurity vulnerabilities in their vehicles. Some manufacturers have started to implement measures to enhance the security of their systems, such as encrypting data transmissions and incorporating more robust authentication protocols. Additionally, there is a growing emphasis on the need for regular software updates and patches to address known vulnerabilities.
Regulatory bodies are also playing a crucial role in enforcing stricter cybersecurity standards. Agencies like the National Highway Traffic Safety Administration (NHTSA) and similar organizations worldwide are working to develop guidelines and regulations to ensure that vehicle manufacturers prioritize cybersecurity. However, as technology continues to evolve, there is a need for ongoing collaboration between industry stakeholders and regulatory bodies to keep pace with emerging threats.
Preventive Measures and Future Directions

Improving TPMS Security
To bolster TPMS defenses, manufacturers should focus on implementing encryption and authentication measures to protect data transmissions. By encrypting the signals between tire sensors and the vehicle’s central system, manufacturers can make it significantly harder for hackers to intercept and manipulate the data. Additionally, incorporating authentication protocols can ensure that only authorized devices can communicate with the TPMS.
Regular software updates and patches are also critical in addressing security vulnerabilities. Manufacturers should establish processes for identifying and addressing vulnerabilities as they arise, ensuring that their vehicles remain protected against the latest threats. Industry experts advocate for a proactive approach to cybersecurity, emphasizing the importance of staying ahead of potential threats.
Consumer Awareness and Action
Vehicle owners play a crucial role in maintaining the security of their cars. By staying informed about potential cybersecurity threats and taking proactive measures, consumers can help protect themselves against cyber attacks. Steps such as regularly updating vehicle software, using secure key fobs, and being cautious of suspicious activity can all contribute to improved vehicle security.
Public awareness campaigns can also play a significant role in educating consumers about vehicle cybersecurity. By increasing awareness of the risks associated with connected cars, these campaigns can empower consumers to take action and demand better security measures from manufacturers. As more people become aware of the potential threats, the pressure on automakers to prioritize cybersecurity will continue to grow.
The Role of Legislation and Regulation

Current Regulatory Landscape
The current regulatory landscape for vehicle cybersecurity is still evolving, with various initiatives underway to address the vulnerabilities associated with connected cars. In the United States, the NHTSA has issued guidelines for vehicle cybersecurity, encouraging manufacturers to adopt best practices to protect against potential threats. However, gaps remain in the regulatory framework, particularly concerning the enforcement of these guidelines.
Internationally, similar efforts are being made to establish standards for vehicle cybersecurity. The United Nations Economic Commission for Europe (UNECE) has developed a framework for automotive cybersecurity, which aims to standardize practices across countries. However, the implementation and enforcement of these standards vary, highlighting the need for ongoing collaboration between international regulatory bodies.
Potential Policy Solutions
To address the vulnerabilities associated with TPMS and other vehicle systems, policymakers must consider implementing new regulatory measures. Proposals for stricter cybersecurity standards include mandating encryption for all wireless communications in vehicles and requiring manufacturers to conduct regular security assessments. Additionally, there is a need for clear guidelines on how to respond to and report cybersecurity incidents.
International cooperation is also crucial in setting cybersecurity standards for vehicles. By working together, countries can develop a unified approach to addressing the challenges posed by connected cars, ensuring that all vehicles meet a minimum level of security. This collaborative effort can help create a safer and more secure environment for consumers worldwide.