
Keylogging is a cybersecurity threat that can compromise your personal information by recording your keystrokes. Whether it’s through software or hardware, keyloggers can be stealthy, making it difficult to detect them. Here are five ways your keyboard might be keylogged, helping you understand the signs and take necessary precautions.
Suspicious Software Installations

One of the most common ways to end up with a keylogger on your system is through malicious software installations. These programs often masquerade as legitimate applications, tricking users into downloading them. Once installed, they can start monitoring your keystrokes silently. Always ensure that you download software from trusted sources and keep your antivirus software up to date to detect and remove potential threats.
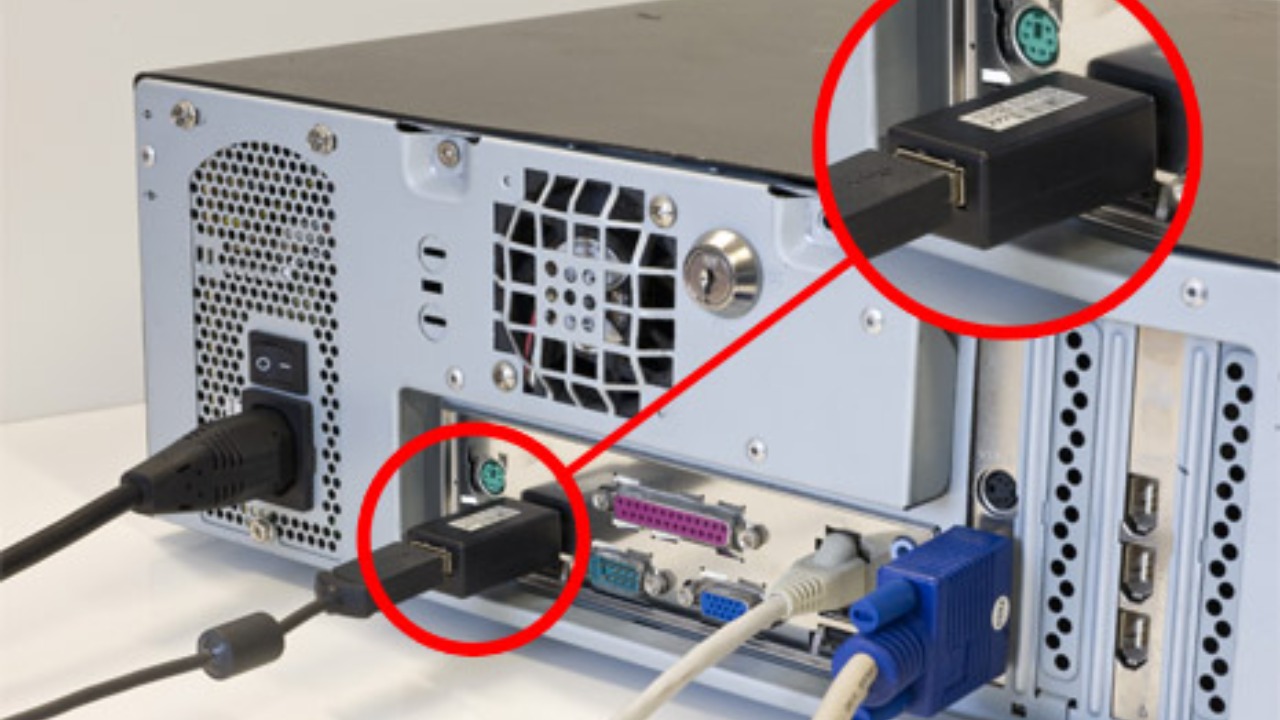
Unauthorized Hardware Devices

Physical keyloggers are small devices that can be easily attached to your keyboard’s connector without your knowledge. These hardware devices can capture keystrokes by sitting between your keyboard and your computer. Regularly check your keyboard connection to ensure no unfamiliar devices are present. In shared or public spaces, be particularly cautious of any unexpected changes to your hardware setup.
Unexpected Network Activity

Keyloggers often transmit collected data to remote servers, which can lead to unusual network activity. If you notice an increase in data usage or strange connections in your network logs, it may be a sign of a keylogger at work. Utilize firewall software and network monitoring tools to identify and block unauthorized transmissions. Monitoring your network activity can help you catch keyloggers in action, preventing potential data breaches.
Abnormal Keyboard Behavior

Keyloggers can sometimes cause your keyboard to behave erratically, such as input lag, unexpected keystrokes, or non-responsive keys. These issues might indicate software interference from a keylogging program. If you experience such problems, perform a comprehensive scan with your security software and consider resetting your keyboard drivers. Anomalies in keyboard performance can serve as an early warning sign, prompting further investigation.
Unfamiliar System Processes
Keyloggers often run as background processes, making them difficult to detect. By regularly checking your system’s task manager or process list, you can spot unfamiliar processes that may indicate malicious activity. If you discover processes with suspicious names or high resource usage, research them to confirm their legitimacy. Tools that provide detailed information about running processes can help you identify potential threats and protect your system from unauthorized keystroke logging.