Tech is ever-evolving, yet some misconceptions persist. These myths might seem harmless, but they can lead to misunderstandings about how technology works. From privacy misconceptions to hardware myths, let’s debunk some of the most common tech fallacies.
The Internet is a Cloud in the Sky

The term “cloud” often leads people to imagine data floating around in the sky. In reality, the cloud is just a metaphor for the internet, where information is stored on physical servers located in data centers around the globe. These servers are managed by companies like Amazon, Google, and Microsoft, ensuring that your data is accessible from anywhere, not floating above us.
Macs are Completely Immune to Viruses

There’s a longstanding myth that Macs are immune to viruses, but this is not entirely true. While macOS is built on a Unix-based system, which is generally more secure, Macs can still be vulnerable to malware, phishing attacks, and other security threats. Regular updates and good security practices are essential for Mac users, just as they are for Windows users.
More Megapixels Mean Better Camera Quality

It’s a common belief that more megapixels equate to better image quality, but that’s not the whole story. While megapixels determine the resolution of an image, factors like sensor size, lens quality, and image processing software play a significant role in the overall photo quality. A camera with fewer megapixels can outperform one with more if it has superior technology in other aspects.
Private Browsing Keeps You Totally Anonymous
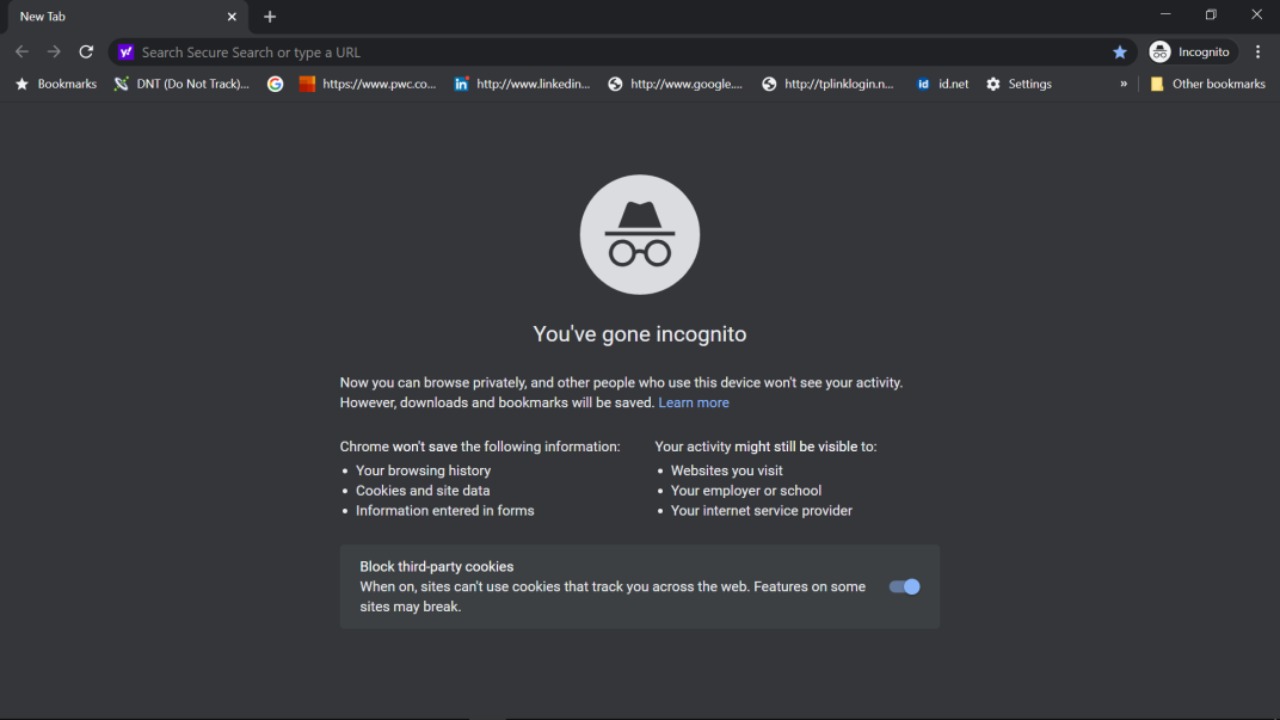
Many believe that using private browsing or incognito mode makes them invisible online. In truth, this mode only prevents your browser from saving your history, cookies, or form data. Your internet service provider, websites, and network administrators can still track your activity. For real anonymity, additional tools like VPNs are necessary.
Closing Apps Saves Your Phone Battery

Contrary to popular belief, closing apps frequently doesn’t necessarily save your phone’s battery. Modern operating systems are designed to manage background apps efficiently. In fact, force-closing apps can sometimes consume more battery as it requires more energy to relaunch them later. Instead, managing settings and updates can better optimize battery life.
Cryptocurrency is a Totally Untraceable Currency

While cryptocurrencies are often thought to be anonymous, they are not entirely untraceable. Most transactions are recorded on a public ledger called a blockchain. Techniques and tools are available to trace these transactions back to individual users, especially when they convert crypto into fiat currency. The idea of untraceable currency is more myth than reality.
More Bars Mean Better Cell Signal

Seeing more bars on your phone doesn’t always mean you have a better or faster connection. Bars indicate signal strength, but not necessarily the quality of the connection. Factors like network congestion and network technology (3G, 4G, 5G) play a crucial role in determining your actual connection quality.
Incognito Mode Hides Your Browsing from Everyone
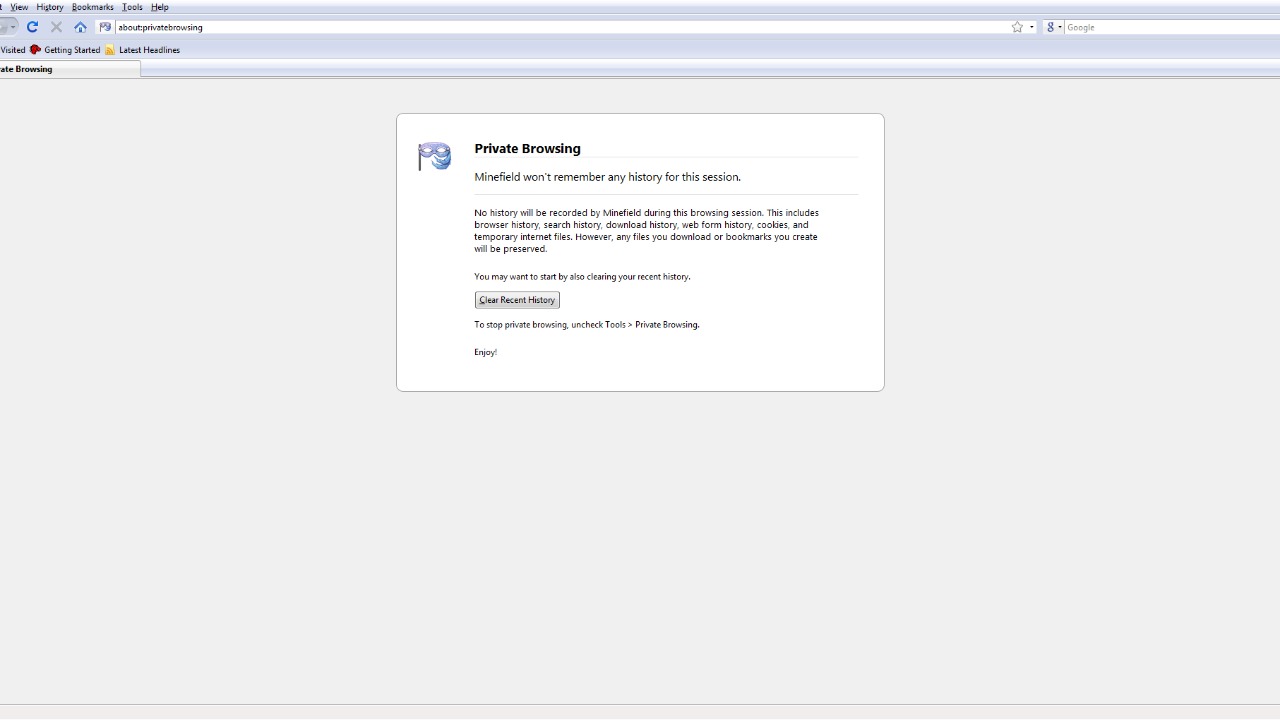
Many users mistakenly believe that incognito mode hides their online activities from all parties. While it does prevent local browsing history from being saved, it doesn’t hide your activity from your employer, ISP, or the websites you visit. For complete anonymity, consider using additional privacy tools.
All Data is Safely Stored in the Cloud

While cloud storage services are generally secure, they are not infallible. Data breaches, server outages, and other technical issues can compromise your data. It’s crucial to regularly back up important data and use strong, unique passwords to enhance your data protection. Relying solely on cloud storage without additional security measures can put your information at risk.